Updated information: If the center window below has a line reading 'Npcap Packet Driver (NPCAP)' or similar, that must remain enabled (checked). This is the packet capture driver for Wireshark and other capture tools
For Gen2 SharkTaps you will see Realtek 8153 instead of Asix 88179. For Gen3, Microchip LAN7801.
Configuring the virtual Ethernet port:
One of the advantages of the USB SharkTap is that you can have virtual Ethernet port dedicated to network sniffing, rather than reconfiguring a port sometimes used for other purposes. The following two setting are not absolutely necessary, but are recommended. The first setting minimizes the number of packets your PC will attempt to transmit over the virtual port. The SharkTap will not route any packets sent from your PC to the Network ports, but Wireshark will still show these packets, which can clutter up a capture. The second setting enables jumbo packets, which is necessary if you are sniffing a link with jumbo packets.
LINUX: On Linux, we recommend that you simply don’t assign an IP to the virtual port. ‘Jumbo packet’ is enabled on Linux by changing the MTU. Example: sudo ifconfig usb0 mtu 4088
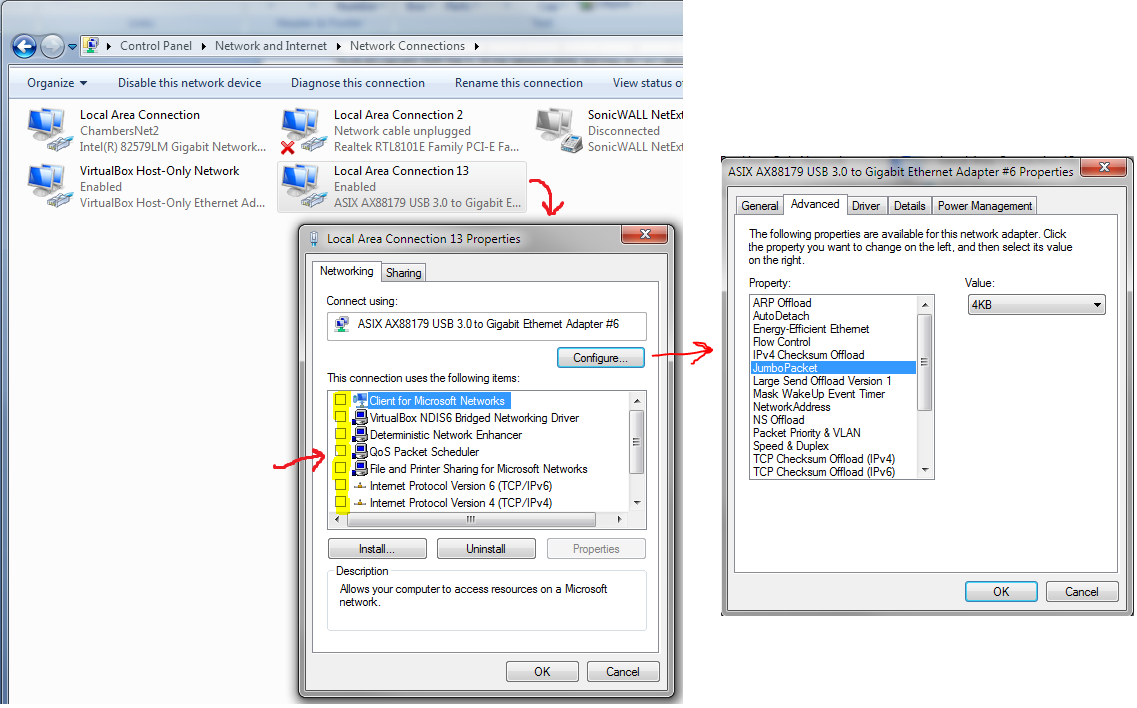
WINDOWS: Go to Control Panel -> Network and Sharing Center -> Change Adapter Settings, which will bring up a window like the one below. Look for the adapter reading ASIX AX88179…, which is “Local Area Connection 13” in the example below. Right click on that and select ‘Properties’, which will bring up the smaller window shown by the first red arrow. Unclick all of the boxes shown in yellow. Then click on ‘Configure’ button, which will bring up the window to the right of the red arrow. Click on the ‘Advanced’ tab, then click on ‘JumboPacket’, then select 4KB.
